- The IDA Pro (Free/ Commercial)
- Ollydbg (Free)
- Immunity Debugger (Free)
- Radare2 (Free)
- x32/64dbg (Free)
- Binary Ninja (Free/ Commercial)
- Windbg (Free)
Using the sample executable files.
x32dbg
Open x32dbg:
Open sample create file executable into x32dbg:
Using F9 key to run once the program:
The entry point for the main function:
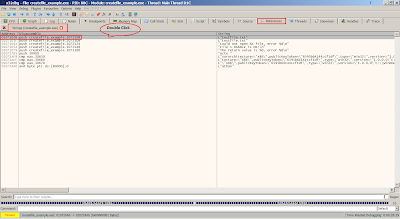
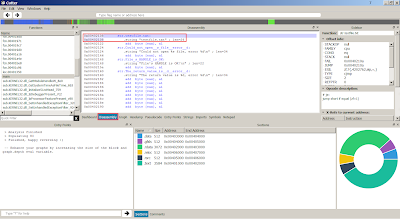
Right click on the disassembly then search for string references on current module:
The string references will appear in References Tab, double click on the disassembly will jump to the offset:
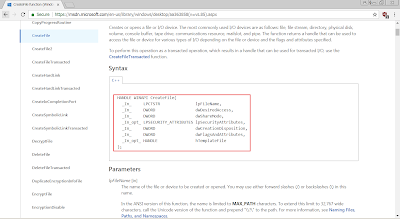
The arguments required by CreateFile function as shown:
The explanation of the CreateFile function can refer back to MSDN:
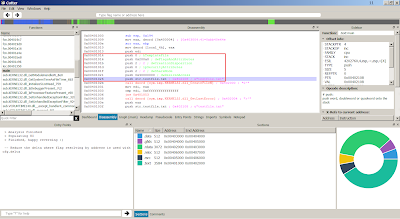
In order to patch the filename, follow the address in dump:
Notice the filename in dump, right click and modify the value:
After successful patch the filename, use F9 to continue run.
Note that the new created filename has changed.
Cutter
Cutter is GUI of radare2.
Open cutter:
Open the sample executable file to analyze:
Search for the main function then double click on it, it will takes you to the disassembly of the main function:
Click on Strings then double click on suspicious strings:
Upon double click, it will jump to the offset of the strings:
Right click on the address and select Show X-Refs:
A X-Refs windows will pop up then double click on the founded:
It will jumps to the address in disassembly view:
Select Graph to view it in Graph mode:
Radare2
Use rabin2 and -z argument to display the strings in executable file:
Use the address obtained from rabin2 in radare2:
Use 'aaa' command to auto analyze the executable file, 'px' command to print the hexdump of the address and 'axt' command to find the code references of the address:
Use 's' command to directly jump to the address and 'pdf' command to print the function in disassembly:
Use 'VV' command to change to graph mode. Use 'q' command to quit visual or graph mode.
Adding the '-w' argument enable the write mode. Patching the binary can use 'w' command.
Note: radare2 will save the patched binary once quit.
Use '-d' argument to debug the program. Use 'dc' command to execute the program. The following will execute the program to the end.
End of Just another Malware Analysis Guide (5) - Reverse Engineering (x32dbg/cutter/radare2)































Reverse engineering is the process of reproducing an existing product in the absence of the original owner. If the original owner stopped producing the product or it is not available in the market. Onsite3D can help you in reverse engineering. Best reverse engineering Calgary, Alberta
ReplyDelete